I recently undertook the process of moving websites to different servers here at work. This required that university networking group scan the new webserver with a tool called Nessus. Unfortunately this turned up several errors, all of them had to do with Secure Sockets Layer or SSL which in Microsoft Windows Server 2003 / Internet Information Server 6 out of the box support both unsecure protocols and cipher suites. These problems would have to be solved before they would allow the new server though the firewalls. The report they university sent me was generated by Nessus generated errors like this:
SSL Version 2 (v2) Protocol Detection
Synopsis :
The remote service encrypts traffic using a protocol with known
weaknesses.
Description :
The remote service accepts connections encrypted using SSL 2.0, which
reportedly suffers from several cryptographic flaws and has been
deprecated for several years. An attacker may be able to exploit
these issues to conduct man-in-the-middle attacks or decrypt
communications between the affected service and clients.
See also :
http://www.schneier.com/paper-ssl.pdf
http://support.microsoft.com/kb/187498
http://www.linux4beginners.info/node/disable-sslv2
Solution :
Consult the application's documentation to disable SSL 2.0 and use SSL
3.0 or TLS 1.0 instead.
Risk factor :
Medium / CVSS Base Score : 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Nessus ID : 20007
----------------------------------------------------------
SSL Medium Strength Cipher Suites Supported
Synopsis :
The remote service supports the use of medium strength SSL ciphers.
Description :
The remote host supports the use of SSL ciphers that offer medium
strength encryption, which we currently regard as those with key
lengths at least 56 bits and less than 112 bits.
Note: This is considerably easier to exploit if the attacker is on the
same physical network.
Solution :
Reconfigure the affected application if possible to avoid use of
medium strength ciphers.
Risk factor :
Medium / CVSS Base Score : 4.3
(CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N)
Plugin output :
Here are the medium strength SSL ciphers supported by the remote server :
Medium Strength Ciphers (>= 56-bit and < 112-bit key)
SSLv2
DES-CBC-MD5 Kx=RSA Au=RSA Enc=DES(56) Mac=MD5
SSLv3
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
TLSv1
EXP1024-DES-CBC-SHA Kx=RSA(1024) Au=RSA Enc=DES(56) Mac=SHA1 export
EXP1024-RC4-SHA Kx=RSA(1024) Au=RSA Enc=RC4(56) Mac=SHA1 export
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Nessus ID : 42873
--------------------------------------------------------------------
SSL Weak Cipher Suites Supported
Synopsis :
The remote service supports the use of weak SSL ciphers.
Description :
The remote host supports the use of SSL ciphers that offer either weak
encryption or no encryption at all.
Note: This is considerably easier to exploit if the attacker is on the
same physical network.
See also :
http://www.openssl.org/docs/apps/ciphers.html
Solution :
Reconfigure the affected application if possible to avoid use of weak
ciphers.
Risk factor :
Medium / CVSS Base Score : 4.3
(CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N)
Plugin output :
Here is the list of weak SSL ciphers supported by the remote server :
Low Strength Ciphers (< 56-bit key)
SSLv2
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
SSLv3
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
TLSv1
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Other references : CWE:327, CWE:326, CWE:753, CWE:803, CWE:720
Nessus ID : 26928
-----------------------------------------------------------------
These three error messages pretty much mean that you need to turn off SSL 2.0 due to exploits that were found after the standard was created. You need to turn off any encryption suites lower than 128bits. The third error message says we need to turn off anything for less than 56bits, but this will be accomplished by turning of anything less than 128bits. Basically your are modifying the settings that restrict the use of specific protocols and ciphers that are used by the schannel.dll. More detailed information can be found at Micorsoft’s KB187498 or KB245030
Disabling SSL 2.0 on IIS 6
- Open up “regedit” from the command line
- Browse to the following key:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server - Create a new REG_DWORD called “Enabled” and set the value to 0
- You will need to restart the computer for this change to take effect. (you can wait on this if you also need to disable the ciphers)
Disable unsecure encryption ciphers less than 128bit
- Open up “regedit” from the command line
- Browse to the following key:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\DES 56/56 - Create a new REG_DWORD called “Enabled” and set the value to 0
- Browse to the following key:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 40/128 - Create a new REG_DWORD called “Enabled” and set the value to 0
- Browse to the following key:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128 - Create a new REG_DWORD called “Enabled” and set the value to 0
- Browse to the following key:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128 - Create a new REG_DWORD called “Enabled” and set the value to 0
- You will need to restart the computer for this change to take effect.
How to verify the changes?
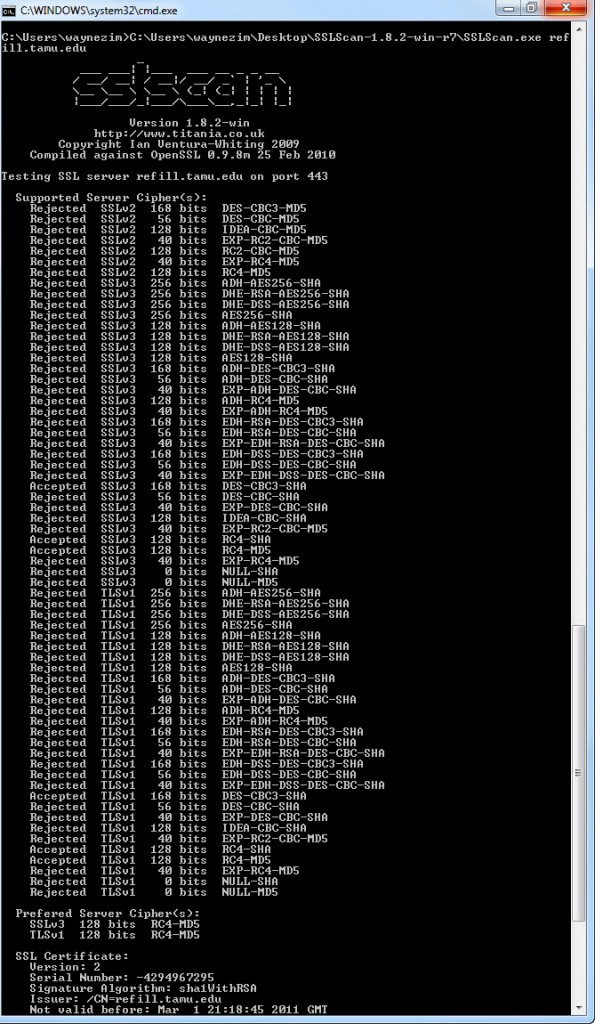
Now that you have made these changes how can you be sure that they have taken place without having to go to your boss or higher authority just to find that you did them wrong. Well I found a nice tool called SSL-SCAN which you can download at http://code.google.com/p/sslscan-win/ for the Windows port or you can download an compile for your favorite operating system at the original project SSL-SCAN site http://sourceforge.net/projects/sslscan/. This tool provides some great detail about what is allows and not allows plus some analysis of the SSL certificate itself.
Below the screen shot shows that we have disabled any ciphers that attempt to use the SSL 2.0 protocol and we’ve disabled all ciphers that less than 128bit.